
Introduction:
- This post will teach you some best practices for increasing the security of your Android apps.
- Android security is unreliable. As a developer, you are unaware of the security level of your application. Every system can be broken, but you can make the hacker’s life much more difficult.
- If you are creating a more complex app, it is your obligation to secure it and preserve your users’ privacy. I’m going to highlight a few of the best practices you can use to create a safe Android app in this article that doesn’t leak data or permissions and is, in general, less susceptible to malicious apps that could be installed on the user’s device.
1. Keep sensitive data on internal storage:
- Every Android app has an internal storage directory attached to it, and the directory’s path is determined by the app’s package name. Because they by default use the MODE PRIVATE file creation mode, the files contained in this directory are extremely safe. This indicates that no other program on the device will be able to access the data. Therefore, the internal storage directory is the ideal location to store all of your app’s sensitive data.
- It is advised that you utilize the getFilesDir() method to get the internal storage directory’s absolute path. Referencing files inside it is as easy as referencing files inside any other directory once you know its location. Here’s an example of how to refer to a file called “myfile.dat” in your app’s internal storage directory:
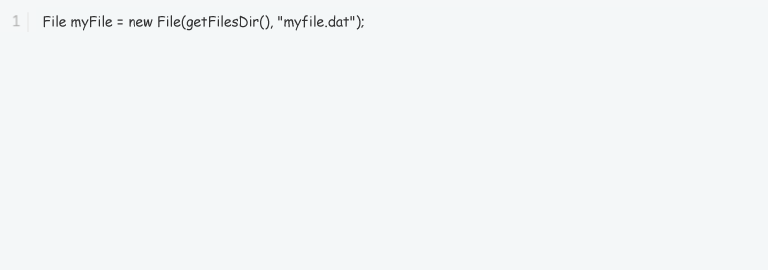
2. Encrypt External Storage Data:
- The internal storage space of an Android device is frequently limited. As a result, sometimes you could be forced to save critical data on mobile storage devices like an SD card.
- It’s critical that you save data on external storage devices in an encrypted way because both users and other apps on the device have direct access to it. AES, which stands for Advanced Encryption Standard and has a key size of 256 bits, is one of the most widely used encryption algorithms in use today.
- It can be difficult to write code to encrypt and decode your app’s data using the javax.crypto package, which is supplied with the Android SDK. Because they are typically considerably simpler to use, third-party libraries like Facebook’s Conceal library are preferred by the majority of developers.
3. Make use of Intents for IPC:
- When developing Android applications, experienced programmers frequently try to asynchronously connect with other apps on an Android device by using sockets, named pipes, or shared files. These methods are not only crude and unattractive but also critical to risks. Utilizing instructions is a simpler and more secure method of interprocess communication on the Android operating system.
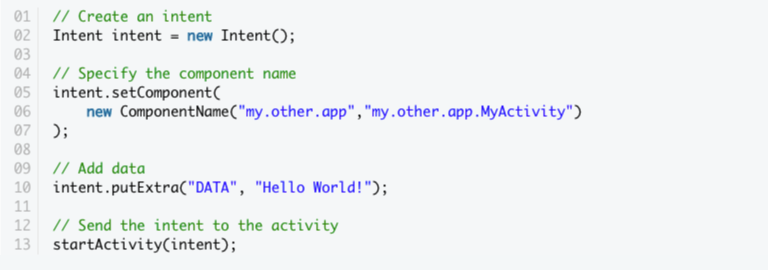
- To send data to a specific app component, build a new instance of the Intent class and use its set component() function to give both the app’s package name and the component’s name. Next, you can use the putExtra() method to add data to it.
- For reference, here’s how you could send the string Hello World to an Activity called MyActivity, which is part of an app called my.other.app:
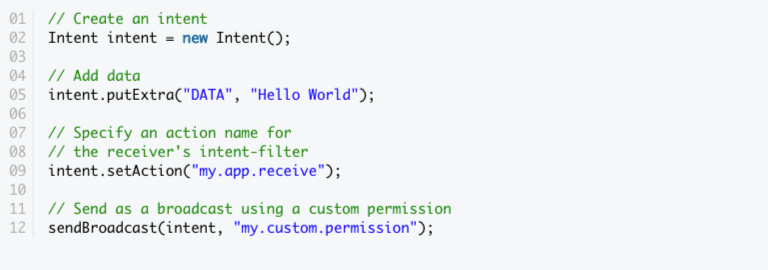
- To deliver data to several apps at the same time, use the sendBroadcast() method to send the intent as a broadcast. But by default, any app with a properly configured BroadcastReceiver can read a broadcast.
- Here is a bit of code that explains how to broadcast the string “Hello World” in a secured way:
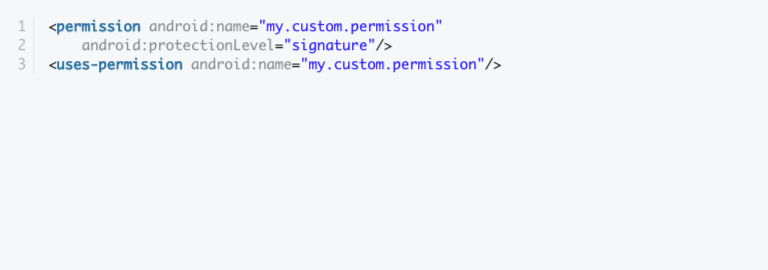
- It should be noted that the above code works as recommended only if the custom permission is specified and utilized in both the sender and recipient apps’ declaration files.
4. Apply HTTPS:
- Your app must always use an HTTPS connection to communicate with your servers, preferably utilizing the HttpsURLConnection class. If you believe that using HTTP for non-confidential data is acceptable, you need to reconsider.
- Every day, many Android users connect to a number of free Wi-Fi networks in public places. These hotspots can include malignant ones. A harmful hotspot can easily modify HTTP traffic’s contents to cause your app to behave unexpectedly, or even worse, it can introduce advertising or bugs into your app.
- By using HTTPS, you can be sure that your network communication is protected against eavesdropping and man-in-the-middle attacks as long as the server is setup with a certificate issued by a trusted certificate authority, such as DigiCert or GlobalSign.
- If your app contains a lot of networking code and you’re worried about accidentally delivering any data as cleartext, you should use Nogotofail, an open source tool created by Google to detect such errors.
5. Use GCM Rather Than SMS:
- Many developers used SMS to transfer data from their servers to their apps back before GCM, or Google Cloud Messaging, was not yet a thing. This technique is largely gone today.
- If you’re one of the developers who hasn’t switched from SMS to GCM yet, you should be aware that neither the SMS protocol is encrypted nor secure from spoofing attacks. Additionally, any app on the user’s device with the READ SMS permission can read an SMS.
- Due to the fact that all GCM communications are encrypted, GCM is much more secure and is the preferred method of pushing messages to an app. On the client side, they are authenticated using often refreshed registration tokens, and on the server side, a special API key.
6. Avoid requesting personal information:
- These days, user privacy is given a lot of attention. In reality, laws like the Personal Information Protection and Electronic Documents Act of Canada and the European Union’s Data Protection Directive require the protection of user privacy. Therefore, you must avoid explicitly requesting sensitive user information in your apps unless you have a strong reason to do so and a protecting architecture.
- Through the Google Identity Platform, user authentication and profile information lookup are more effective on Android. Users may simply sign in to your app with their Google account thanks to the Google Identity Platform. When necessary, your app can quickly look up the user’s name, email address, profile photo, contacts, and other information after a successful sign-in through the platform. You might also use free services like Firebase that will take care of user authentication for you.
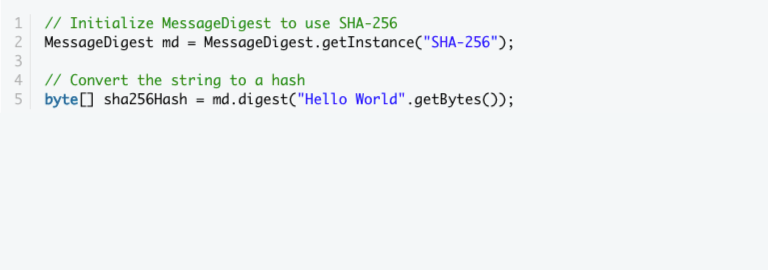
- It is advised to save and provide user credentials in the form of secure hashes if you must manage them yourself. Using the MessageDigest class from the Android SDK is the easiest approach to produce various hashes of different sorts.
- Here is a little piece of code that demonstrates how to use the SHA-256 hashing function to build a hash of the string “Hello World”:
7. Check User Input:
- The majority of the time, buffer overruns and other security problems are not caused by invalid user input on Android. However, you must either use parameterized queries or aggressively clean user input if you want users to be able to interact with an SQLite database or a content provider that utilizes one internally. If you don’t, SQL injection attacks can be used to access your data.
- In a similar vein, user input validation and cleaning are also crucial if you’re using user input to produce code regularly for an embedded scripting engine like Mozilla Rhino.
8. Utilize ProGuard before publishing:
- If hackers manage to obtain the source code, the security features placed into an Android app could be seriously undermined. ProGuard, a tool that is part of the Android SDK, is advised to be used to hide web page source code before publishing your app.
- If the build type is set to release, Android Studio includes ProGuard during the build process by default. Most apps can be protected using the ProGuard default configuration found in the proguard-android.txt file of the Android SDK. A file called proguard-rules. pro, which is a component of every Android Studio project, can be used to add unique rules to the settings.
Conclusion:
I trust that after reading this, you know more about how to secure Android apps. The majority of the best practices I discussed in this article only apply if you create apps using the Android SDK. While developing in the C language, you are expected to manage low-level aspects, such as pointers and memory allocation yourself. If you are using the Android NDK instead, you have to be much more careful.
Do You Need more information?
For any further information / query regarding Technology, please email us at info@varianceinfotech.in
OR call us on +1 630 534 0223 / +91-7016851729, Alternately you can request for information by filling up Contact Us
 Please wait...
Please wait...
Leave a Reply